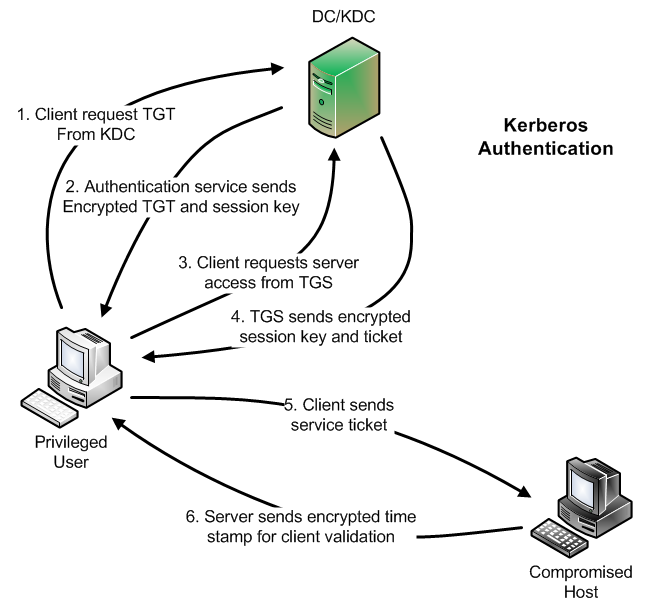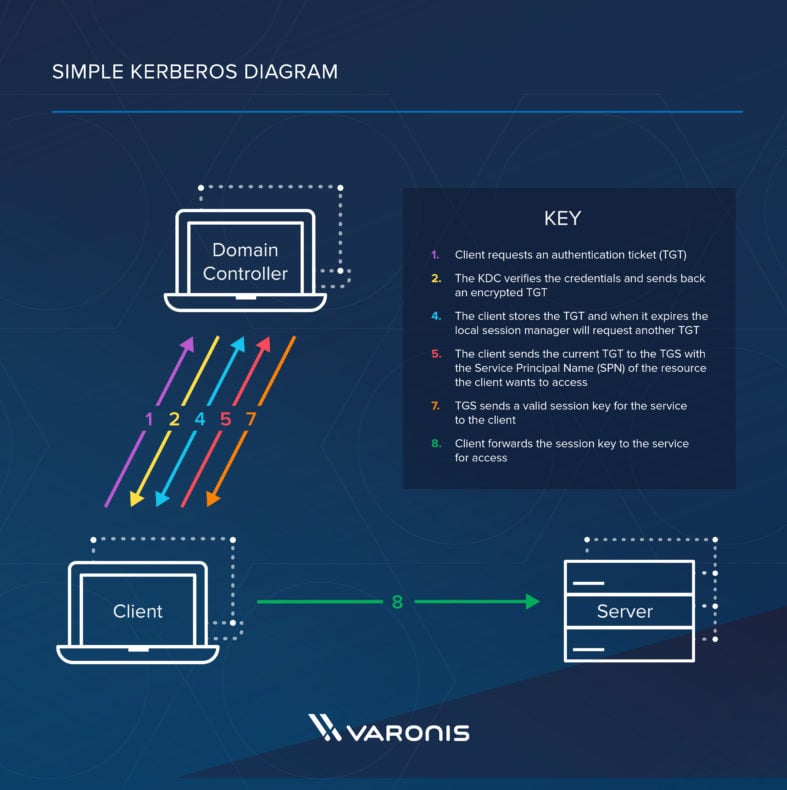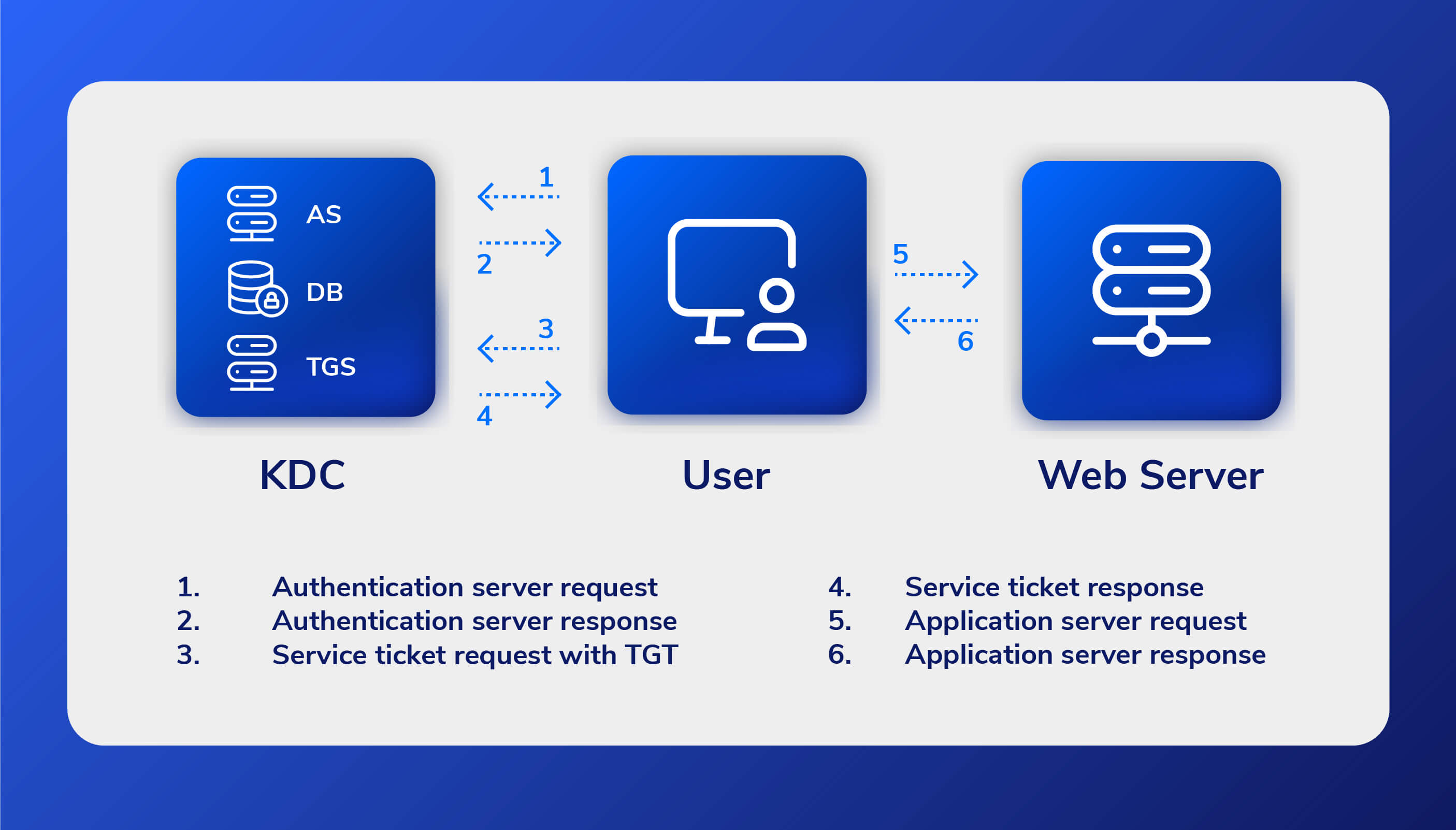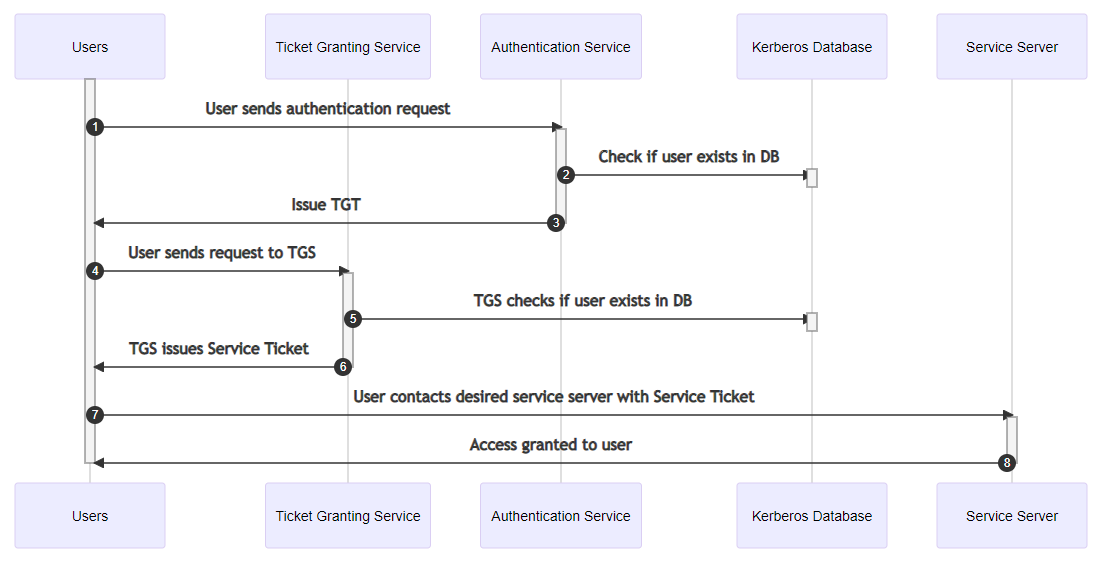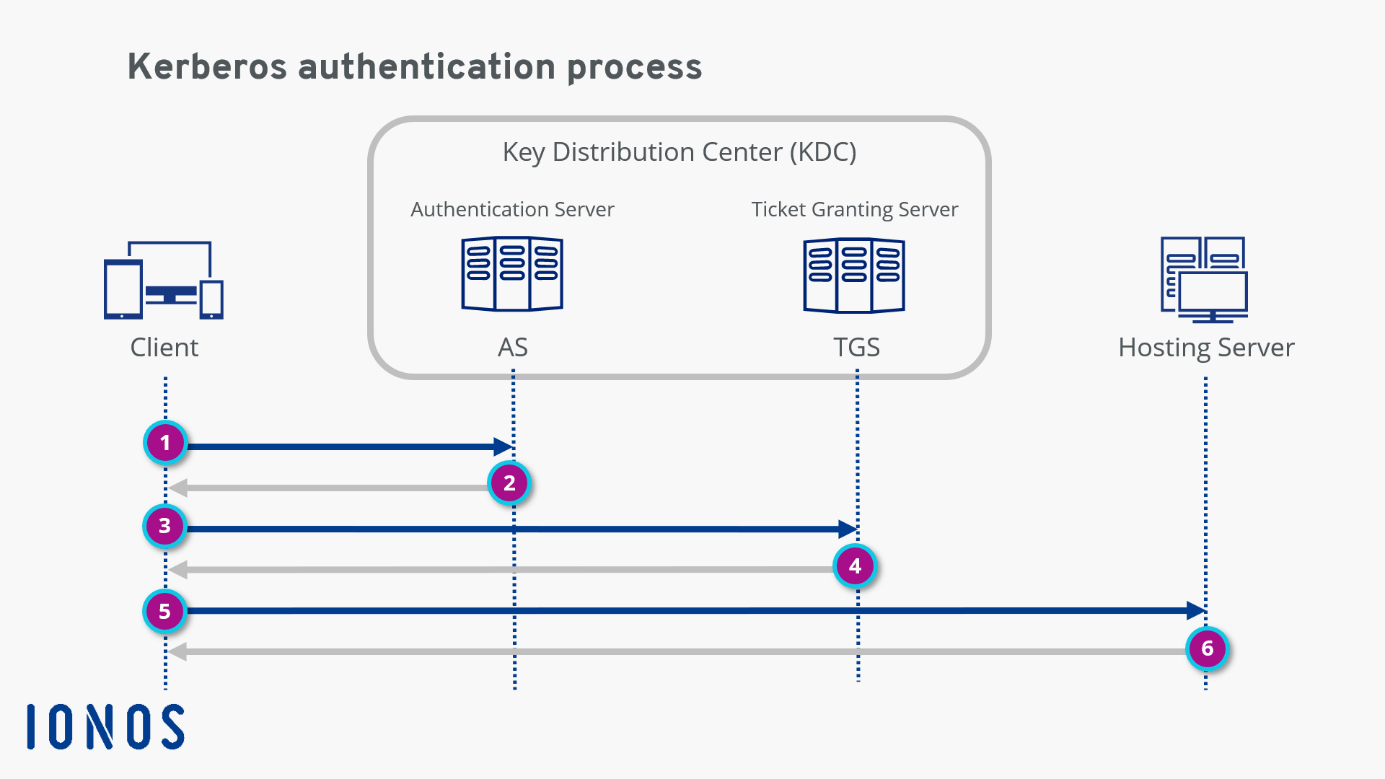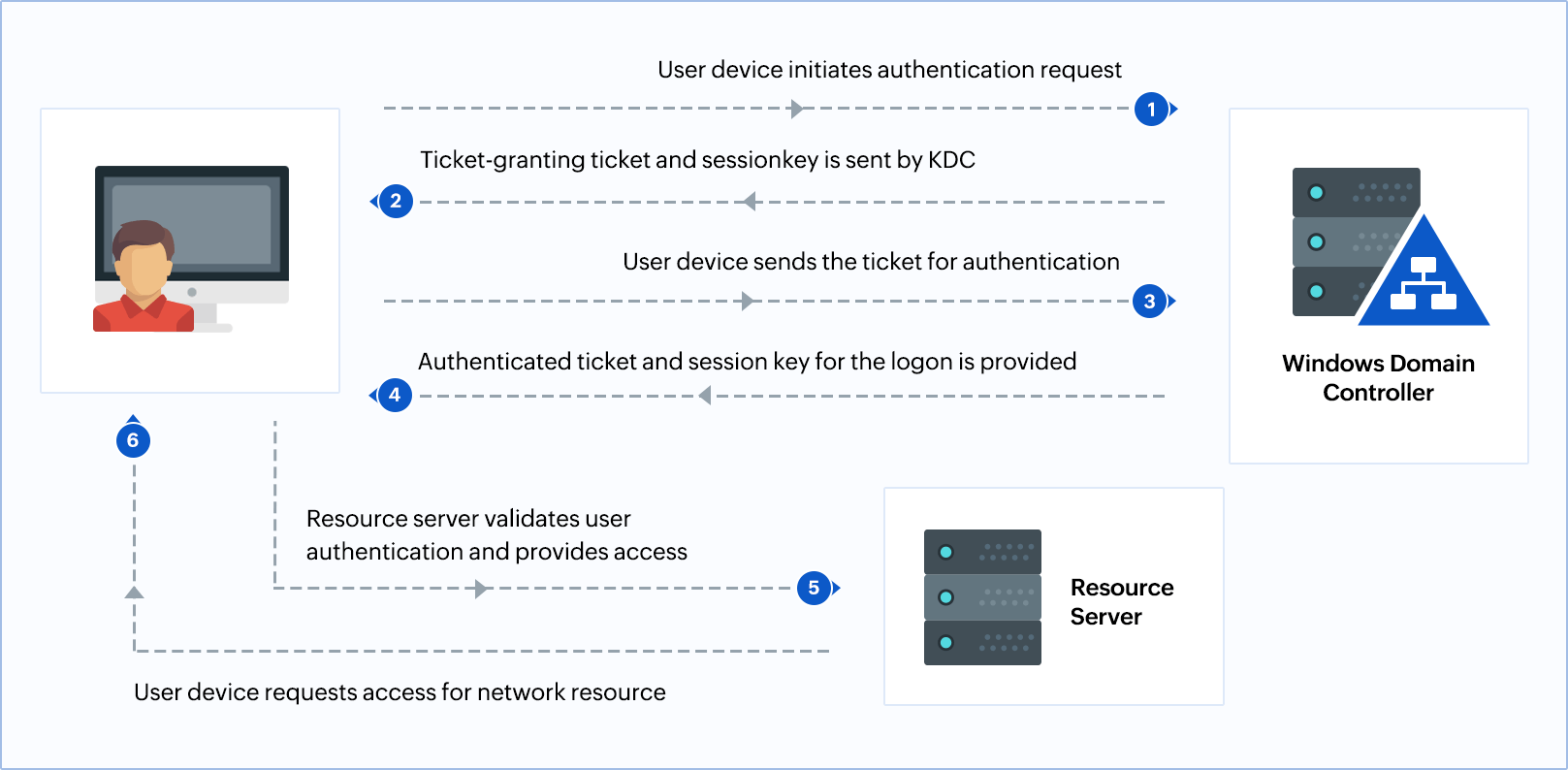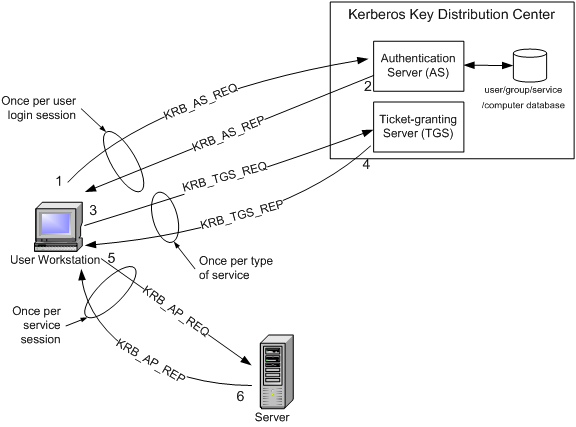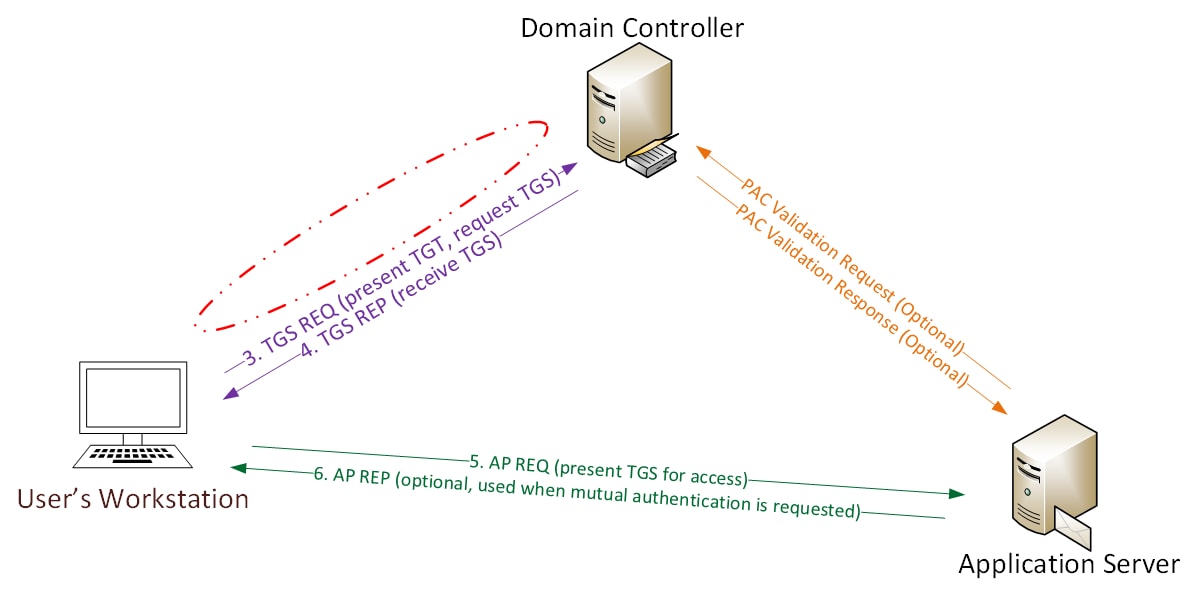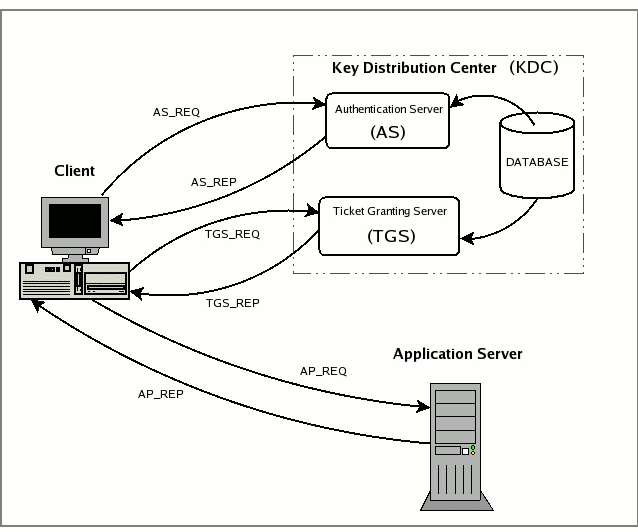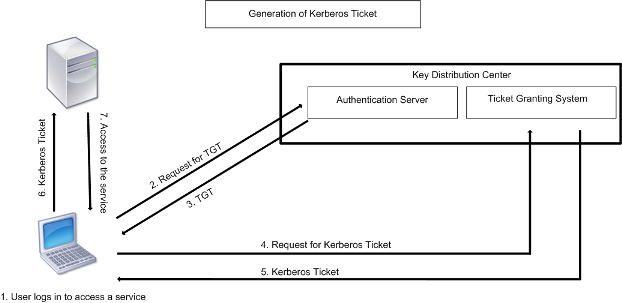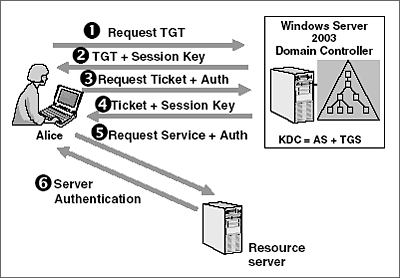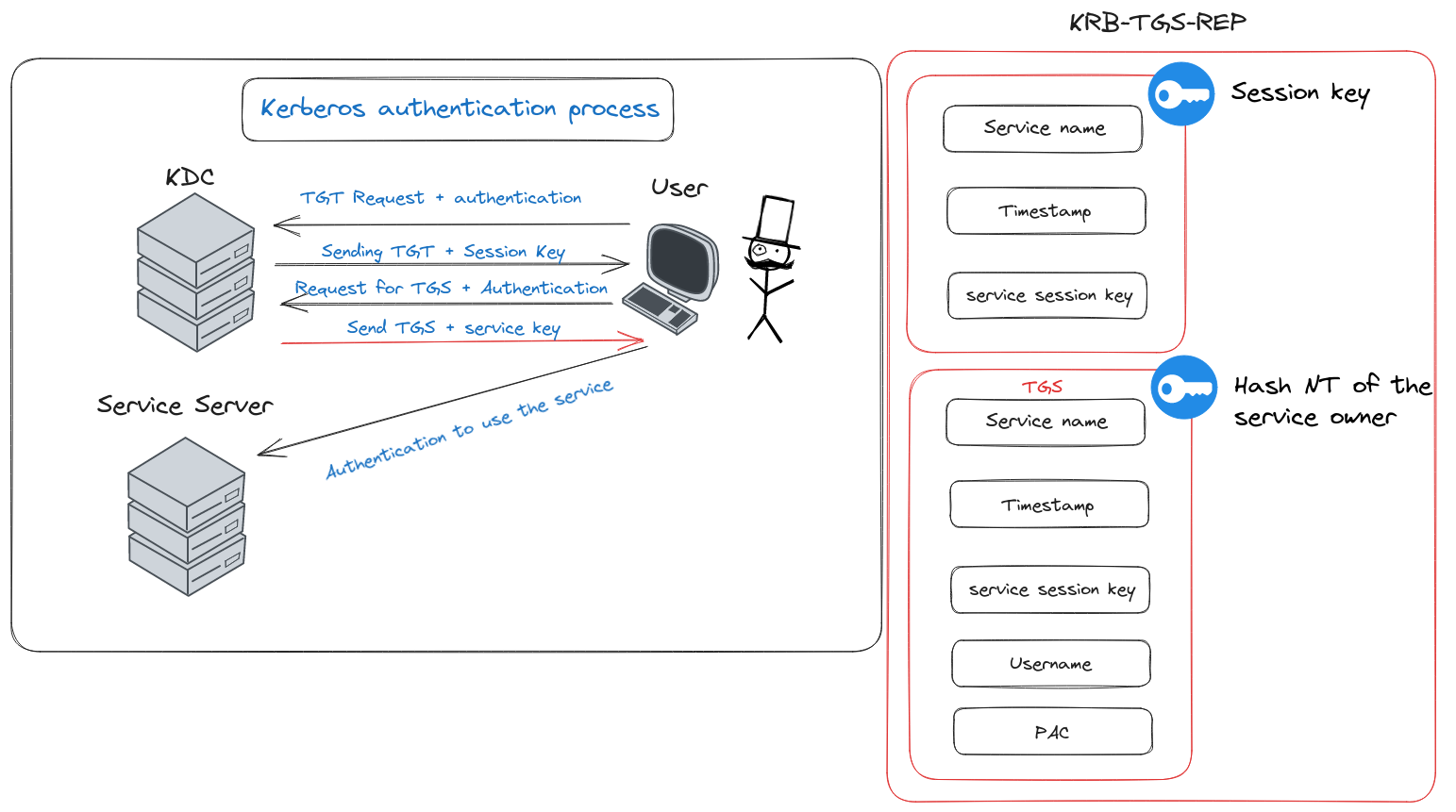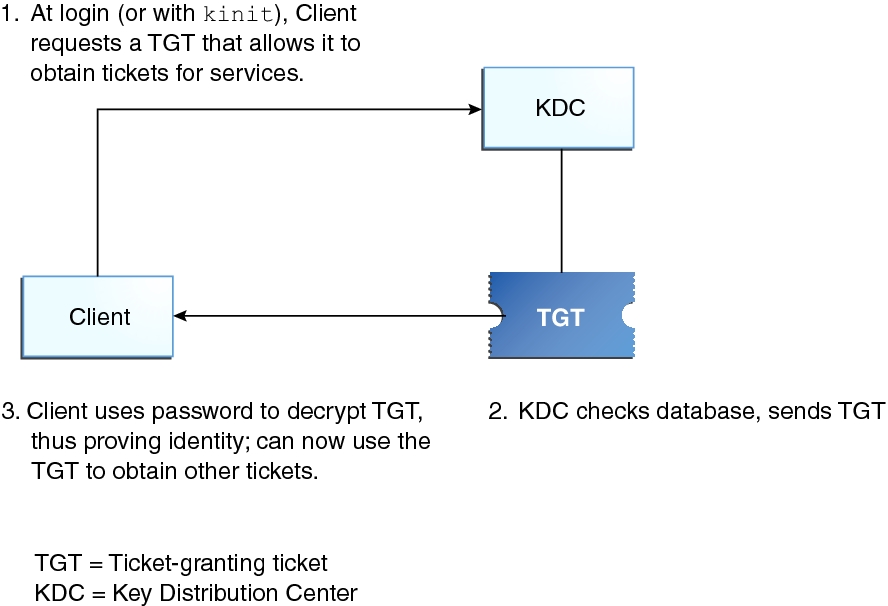
How the Kerberos Service Works - Managing Kerberos and Other Authentication Services in Oracle® Solaris 11.3

1 A simplified version of the Kerberos authentication system: both the... | Download Scientific Diagram
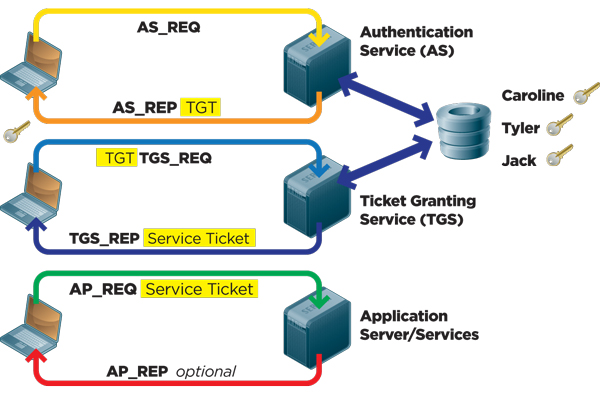
Kerberos Authentication 101: Understanding the Essentials of the Kerberos Security Protocol -- Redmondmag.com